Over $500B currently sits locked in staking across blockchain networks, securing protocols through economic alignment. Yet, many users and validators approach slashing with fear. This fear is understandable: no one wants to lose their staked assets. However, when the actual data is analyzed, a different picture emerges.
Slashing is ultimately a powerful deterrent that rarely needs to be invoked. This analysis examines real-world slashing data across Ethereum, Cosmos, and Polkadot, revealing how uncommon these events are and why this security feature works so effectively despite its infrequent use.
Slashing as Deterrence
Think of slashing as blockchain's version of nuclear deterrence. Just as nuclear weapons prevent war through the threat of catastrophic consequences, slashing mechanisms prevent attacks on PoS networks by making them economically suicidal.
When validators stake assets, they post collateral that can be confiscated if they violate consensus rules. This transforms validation from a risk-free activity into one with meaningful skin in the game. In most cases, a validator’s stake is largely composed of funds delegated by users, meaning the responsibility extends beyond the validator’s own capital. In this case, attacking a network would destroy not just their own stake but also their clients' trust, assets, and future revenues.
Slashing is Rare
Despite the fear it generates, slashing remains exceedingly rare in practice:
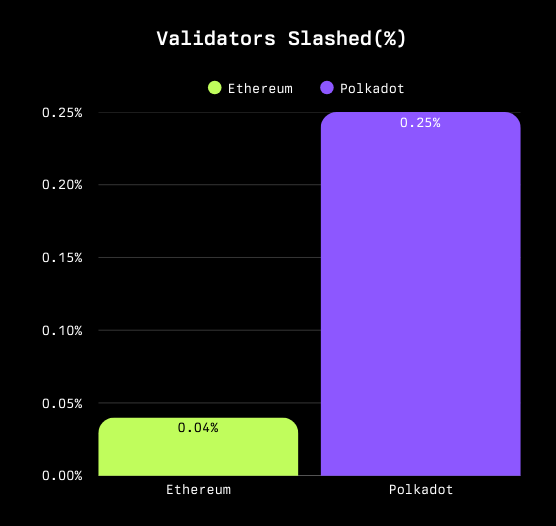
- Ethereum: Only about 0.04% of validators have ever been slashed - 472 out of more than 1,200,000 validators
- Cosmos Hub: In its entire history since 2019, there have been only 5 slashing events for double-signing (a severe offense), underscoring just how rare such incidents are.
- Polkadot: Outside of one notable mass-slashing incident in its early days, Polkadot's slashing rate has been minimal
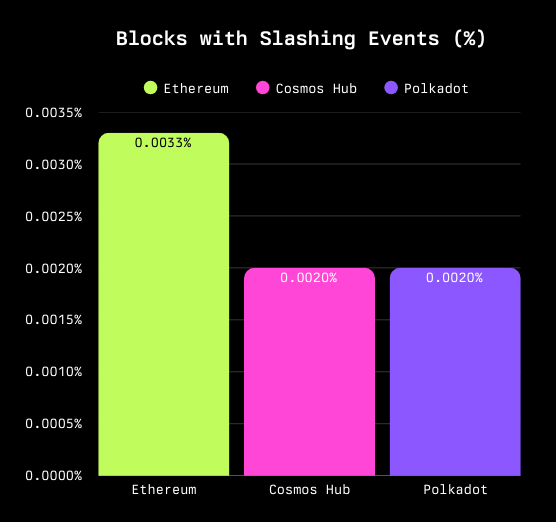
Even more revealing is how often blocks contain slashing events:
- On Ethereum, approximately 0.0033% of blocks include a slashing - roughly 1 in 30,000 blocks
- For Cosmos Hub and Polkadot, this figure is even lower, with slashing events appearing in less than 0.002% of the blocks
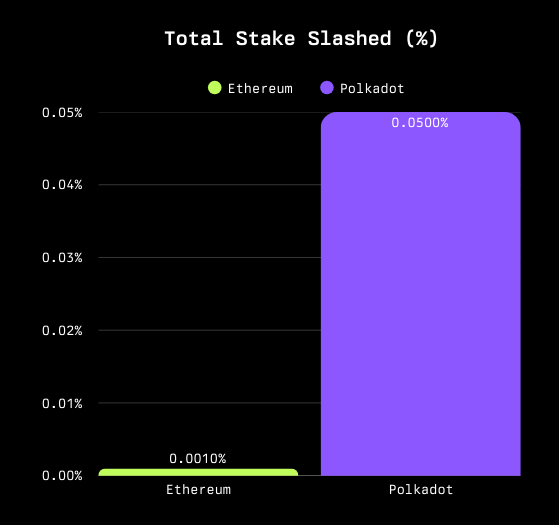
In financial terms, the impact is similarly minuscule. Across major PoS networks, the total percentage of stake ever slashed is well below 0.05% of all staked assets. For Ethereum specifically, it's around 0.001%.
Technical Issues, Not Attacks
What's particularly revealing is that virtually all slashing events result from technical errors rather than malicious attempts to attack networks. The most common causes include:
- Redundancy misconfigurations and key misuse: Running backup nodes without proper safeguards or reusing validator keys across machines, both of which can lead to accidental double-signing
- Client software bugs: Issues in validator clients causing inadvertent rule violations
- Infrastructure outages: Correlated failures during cloud provider downtimes
In practice, slashing primarily punishes misconfigurations and operational mistakes. In fact, there has never been a recorded instance of slashing resulting from a deliberate attack on any major PoS network. The mere presence of slashing as a penalty has effectively deterred such attacks from being attempted.
Network Implementations
While the core concept remains the same, different PoS networks implement slashing with varied philosophies. Each of these is worth exploring due to their varied implementation.
Ethereum's Approach
Ethereum uses a correlation-aware slashing mechanism. An isolated mistake might cost a validator around 1 ETH (about 3-4% of their 32 ETH stake), but if many validators misbehave simultaneously, each loses a larger percentage. This design assumes correlated failures are more likely to be attacks than isolated ones.
Slashed ETH is permanently burned, and the slashing action cannot be reversed by governance - it's entirely algorithmic and automatic.
Cosmos’ Approach
Cosmos takes a more binary approach with predefined penalties: 5% of stake for double-signing (with temporary "tombstoning" or banning of the validator) and, historically, a tiny 0.01% for extended downtime. These parameters are standard defaults across Cosmos SDK-based networks. However, chains can customize or extend them based on their specific risk tolerance and design goals, even if such changes require additional implementation beyond the configuration.
The mechanism is straightforward and predictable, but potentially severe for a single mistake. All slashed ATOM tokens are burned.
Polkadot's Approach
Polkadot employs a graduated slashing system based on offense severity. Isolated failures might receive no slash at all, while coordinated ones (intentional or not) can incur penalties ranging from 0.01% to 100% of stake.
Uniquely, slashed DOT tokens go to the Treasury rather than being burned, allowing governance to potentially reverse slashing decisions if they're deemed erroneous or overly harsh.
Slashing in Symbiotic
As staking expands beyond single-chain architectures, traditional slashing mechanisms begin to show their limitations. Cross-chain protocols require more flexible, programmable systems that can adapt to different asset types, consensus rules, and operational realities.
At Symbiotic, we’ve introduced several novel approaches to allow slashing in a cross-chain context:
Veto Capability
Symbiotic's Veto Slashing feature introduces a two-phase process: when a slashing request is received, there's a designated period during which trusted entities called "Resolvers" can veto the slashing if it appears unwarranted or accidental. This adds a human element to what's otherwise an algorithmic process — and the Resolvers themselves can be configured in flexible ways, from a simple multisig to a fully decentralized DAO, depending on the needs and governance model of the network.
Customizable Burners
Since Symbiotic works with diverse assets, "Burner" contracts are implemented that handle slashed tokens differently depending on their type:
- For regular tokens, burning simply removes them from circulation
- For liquid staking tokens (LSTs), the burner can unwrap them to the underlying asset before burning
- For LP tokens, the burner can withdraw them and burn the underlying assets
Slashing Hooks
Perhaps most innovative are the "Hooks" - customizable callbacks that execute when slashing occurs. These allow for context-specific responses, such as:
- Automatically reducing a slashed operator's future allocation
- Redistributing slashed stake to other operators
- Implementing progressive penalty logic — for example, slashing more severely on second or third offenses to discourage repeat violations.
This programmable approach to slashing allows the mechanism to serve multiple purposes beyond simple punishment.
Why Slashing Works
The effectiveness of slashing stems from core game theory principles. When a validator must stake assets to participate, they enter a system where:
- Honest behavior leads to steady rewards with near-zero risk of slashing
- Dishonest behavior risks substantial financial loss that exceeds potential gains
This aligns incentives for all participants. Even if a network processes billions in transactions, the cost of attacking it (losing billions in staked assets) exceeds the potential profit. The math simply doesn't work for attackers.
But the risks go beyond just capital loss. In delegated staking systems, validators are often responsible for their clients’ funds. A slashing event can trigger a loss of reputation, future revenue, and delegator trust, with long-term consequences that far outweigh the initial penalty.
As a result, slashing has shaped validator behavior toward extreme caution. Professional operators invest heavily in redundancy, monitoring, slashing protection databases, and rigorous operational procedures. Many maintain insurance funds and compensate delegators when slashing occurs. This culture of accountability and resilience strengthens the overall security of PoS networks.
The Power of Deterrence
The data is clear: slashing in proof-of-stake systems is remarkably rare, affecting a tiny fraction of validators and an even smaller percentage of staked assets. When it does occur, it's almost always due to technical errors rather than attacks. In traditional systems, addressing such cases often requires reactive governance proposals or manual rollbacks — a time-consuming and contentious process. Symbiotic’s design introduces a more structured alternative: features like Resolvers and Veto Slashing allow for slashing events triggered by technical errors to be intercepted and reviewed before they take effect onchain, enabling faster and more reliable remediation without compromising the deterrent effect. This is precisely how deterrence should work. The mere possibility of significant financial loss effectively prevents malicious behavior, while the actual frequency of punishment remains low. By making attacks economically irrational, slashing ensures that rational participants will always choose to follow the rules.
For validators, delegators, and protocol builders alike, understanding the true nature of slashing helps dispel unfounded fears and reinforces its role as a foundational security primitive in proof-of-stake systems. It’s not just a mechanism for punishment; it’s a tool for aligning incentives, encouraging operational excellence, and protecting network value. As staking continues to evolve across chains and asset types, slashing will remain a critical and increasingly adaptable safeguard in the decentralized economy.
Sources:
- https://www.mintscan.io/cosmos/validators
- https://services.kjnodes.com/mainnet/cosmoshub/slashboard/#validator-slashes
- https://polkadot.subscan.io/validator_list?status=validator&page=4&page_size=25
- https://explorer.rated.network/slashings?network=mainnet×SlashedPage=1&slashesReportedPage=1
- https://github.com/moondance-labs/tanssi-slash-analysis/blob/main/output/filtered_slashing.csv
- https://everstake.one/crypto-reports/atom-staking-report-cosmos-on-chain-data-analysis-2024
- https://polkadot.js.org/apps/?rpc=wss%3A%2F%2Frpc.polkadot.io#/staking









