Intro
Over $550b currently sits locked in staking across crypto networks, serving an essential function: securing blockchain networks through economic alignment. However, this approach is inherently inefficient and ultimately fragments the overall crypto landscape—assets dedicated to security become isolated and removed from the broader ecosystem, unable to participate in DeFi, governance, or cross-chain activities. This fragmentation forces networks into a fundamental tradeoff between security and capital efficiency.
Shared security resolves this tradeoff through the abstraction of collateral from underlying security functions. The approach builds elegantly on two core primitives from traditional staking systems: stake verification and slashing penalties. This abstraction unlocks a vast new design space for blockchain systems. While not exhaustive, this research aims to explore this design space through practical case studies, demonstrating the potential that Symbiotic and broader collateral abstraction mechanisms can unlock.
Symbiotic vaults, built on top of existing staking systems, enable any asset to serve as collateral while maintaining its full functionality—whether that's staked ETH participating in DeFi, governance tokens maintaining voting rights, or complex derivatives from other blockchain ecosystems. The system's architecture employs specialized burner contracts to handle stake evaluation and slashing, ensuring robust security guarantees even with complex, multi-utility assets. Understanding the implications of this design starts with examining its foundational concept: stake itself.
What is stake, anyway?
Stake creates economic alignment through verifiable commitments. While traditionally limited to native tokens, Symbiotic enables any asset to serve as stake through native or oracle-based evaluation.
Stake serves as a direct measure of trust by guaranteeing honesty through economic alignment. When participants act in the network's best interest, they gain economically; when they act against it, they face penalties. This core security principle requires that the cost of attacking the network consistently exceeds potential rewards. Such alignment can be achieved either through mere possession (soft alignment) or through direct access requirements (traditional staking).
Traditional staking implementations lock a network's native token within the system and assign it to operator balances. This basic model incorporates two essential security features: time-locked withdrawals and slashing conditions for improper behavior. Yet the concept of stake can extend beyond native tokens to encompass more sophisticated instruments, including derivatives, DeFi positions, and other complex assets.
For analytical purposes, these instruments are collectively defined as 'assets,' with their tokenized representations described as "abstracted stake". Symbiotic vaults accept any wrapped ERC20 token as stake, evaluating them through either native or oracle-based systems.
Native token evaluation follows two paths: direct acceptance, which measures the staking derivative's value in its own units, or pegged acceptance, which maintains a 1:1 relationship with another token. DeFi positions and other dynamic assets introduce additional complexity, often requiring active management to maintain their ETH peg. To ensure stability, these systems can be supplemented with additional mechanisms such as deposits or insurance layers.
Oracle-based evaluation offers an alternative framework for managing abstracted stake. This approach allows networks to leverage oracle-reported values for both stake verification and reward calculations. While implementations range from simple view functions to dedicated attestation networks, the key design challenge lies in striking the right balance between reliable value reporting and efficient propagation.
Cross-network scenarios introduce distinct challenges in stake value management. While assets from external networks maintain their value data in their source networks, they must remain accessible within the Middleware layer on Ethereum. This requires reliable value transmission pathways between the source networks and points of stake utilization.
DeFi Position
Uniswap V3 positions demonstrate how complex DeFi assets can serve as stake through precise valuation formulas and flexible burning mechanisms.
Uniswap V3 positions provide an excellent case study utilizing complex DeFi assets as stake, as they combine precise mathematical valuation with dynamic market-driven values. Consider a position in an X/Y pair (where X represents USD and Y represents ETH), evaluated in terms of X within the price interval [p_a, p_b]. The position's value in USD follows three distinct formulas depending on the current price p:
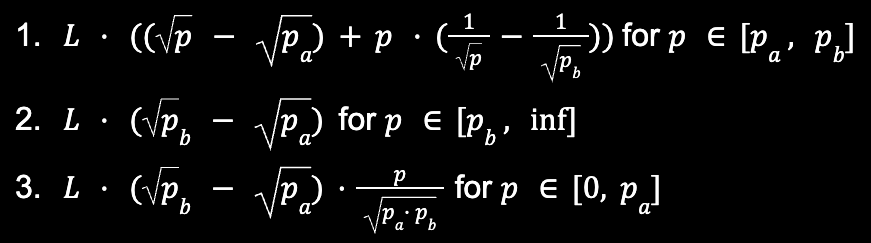
These formulas capture fundamental position dynamics: value increases with Y until reaching a constant, while decreasing without bound as Y falls. While the base calculations exclude accumulated rewards, these can be incorporated through supplementary smart contract logic. This formula can be utilized in an oracle system to track the value of stake.
An LP position is a single-token share representation of an automated market maker pool. In Uniswap’s case, it is represented as an NFT. Like any other sort of asset, it can be used as stake in Symbiotic, as long as it is slashable. The Symbiotic vault system implements Burner contracts to handle slashing events for such positions through three mechanisms:
- Direct share burning: Eliminating position shares
- Position unwinding: Converting to underlying tokens before burning
- Token exchange and burn: Converting to specified tokens with economic modeling to prevent perverse incentives
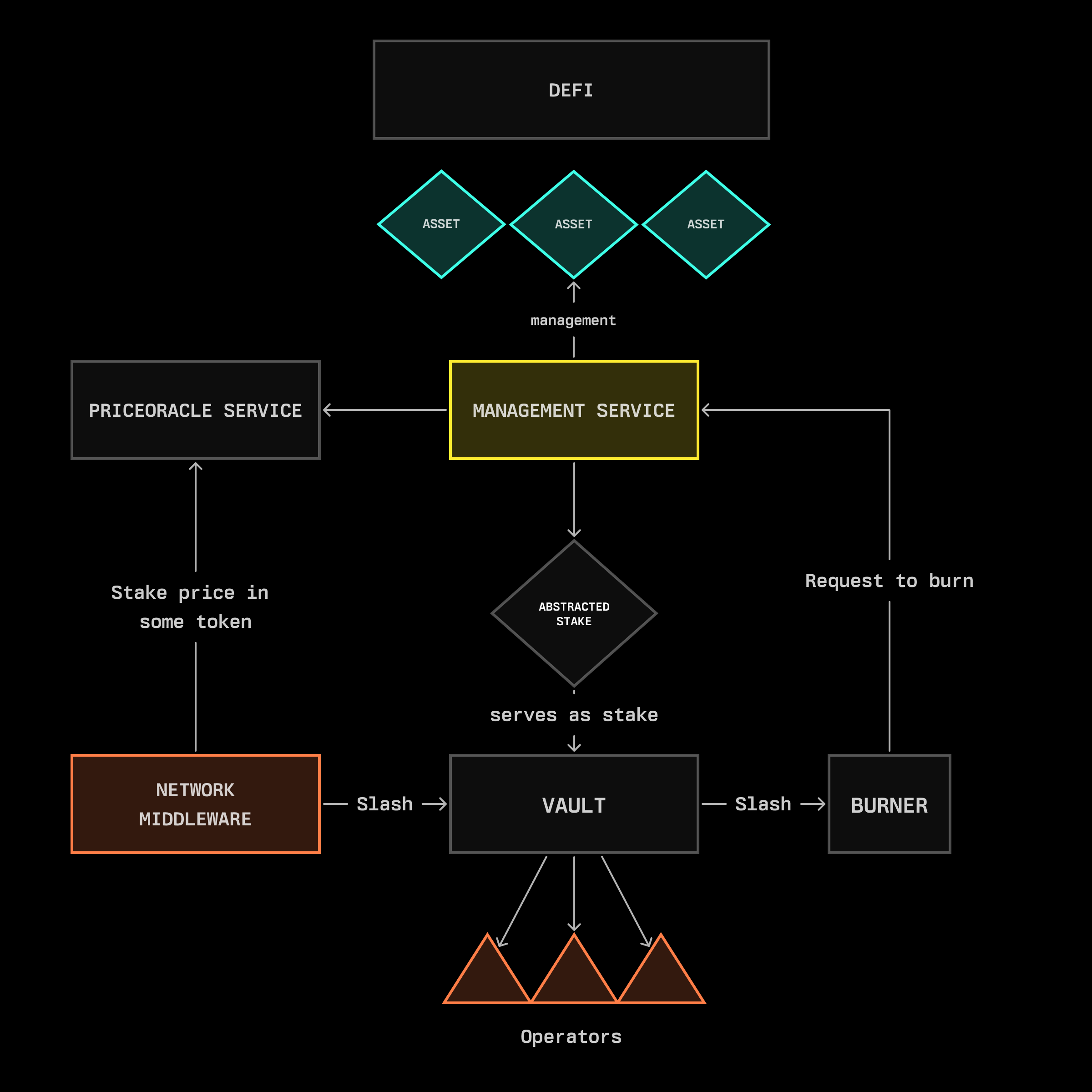
The Burner system is also flexible enough to enable further optimizations, such as:
- Derivative tokens with built-in insurance mechanisms that absorb slashing penalties while preserving position continuity
- Active position management options that improve capital efficiency while introducing carefully bounded counterparty risk
We’ll dive deeper into burners in a separate blog post.
Cross-Network Staking
Cross-network staking enables assets to remain in their origin networks while securing destination networks through synthetic representations and bridge protocols.
Cross-network staking expands capital efficiency beyond single-network boundaries. While traditional bridging requires tokens to be moved between networks for delegation, Symbiotic vaults can integrate directly with bridge protocols to enable native-network asset utilization. This opens up opportunities to use assets beyond the EVM.
The core implementation challenge lies in cross-network slashing. Symbiotic vaults deploy custom burner contracts that handle slashing requests across network boundaries, with bridge protocols executing corresponding token burns in origin networks. Slashing operates asynchronously, converting local abstracted burns to origin-network token burns.
This mechanism demonstrates a core principle of collateral abstraction: physical tokens remain in their origin network while abstracted representations serve as stake in the destination network. The slashing process operates asynchronously through bridge protocols, converting local abstracted burns into real token burns in the origin network. While these origin-network burns aren't strictly necessary—the tokens could simply become inactive—this implementation showcases the flexibility of the burner system in handling cross-network stake management.
This base design can extend further through multi-layer token utilization. As shown in the diagram, native tokens could convert to stTokens to participate in DeFi on the origin network, while simultaneously minting rsTokens—restaked derivatives bridged to Ethereum for Symbiotic vaults. These rsTokens would either maintain 1:1 parity or implement oracle-based valuation depending on protocol requirements.
The stToken valuation can derive from DeFi pool pricing or LST protocol parameters, with a critical focus on modeling value fluctuations during slashing events. Historical slashing patterns and projected magnitudes inform risk parameter design.
The cross-network communication architecture prioritizes three critical aspects:
- Message routing topology
- Propagation latency
- Trust minimization
In addition to connecting completely isolated networks, rollup networks provide an optimal implementation, leveraging the existing native Ethereum communication channels. Slashing events flow through the InputBox contract directly to the network's LST protocol, creating trust-minimized execution paths with predictable finality guarantees. While the previous examples demonstrate efficient cross-network stake management, the principles of collateral abstraction extend beyond simple token transfers or DeFi positions. Network-native assets, particularly governance tokens, present unique opportunities for stake utility expansion. By examining their implementation, we can explore how collateral abstraction enables the simultaneous utilization of the same assets across multiple protocol functions.
Governance tokens
Symbiotic enables governance tokens to simultaneously serve multiple functions - maintaining voting rights and vesting schedules while providing stake security.
Governance tokens present a distinct opportunity to improve efficiency through collateral abstraction. These tokens prioritize in-protocol utility: governance through voting, strategic alignment through vesting, and security through staking, such as in a safety module. Previously, holders had to choose between governance participation or opt-out to participate in DeFi. Collateral abstraction unifies all of these functions, making governance tokens more useful.
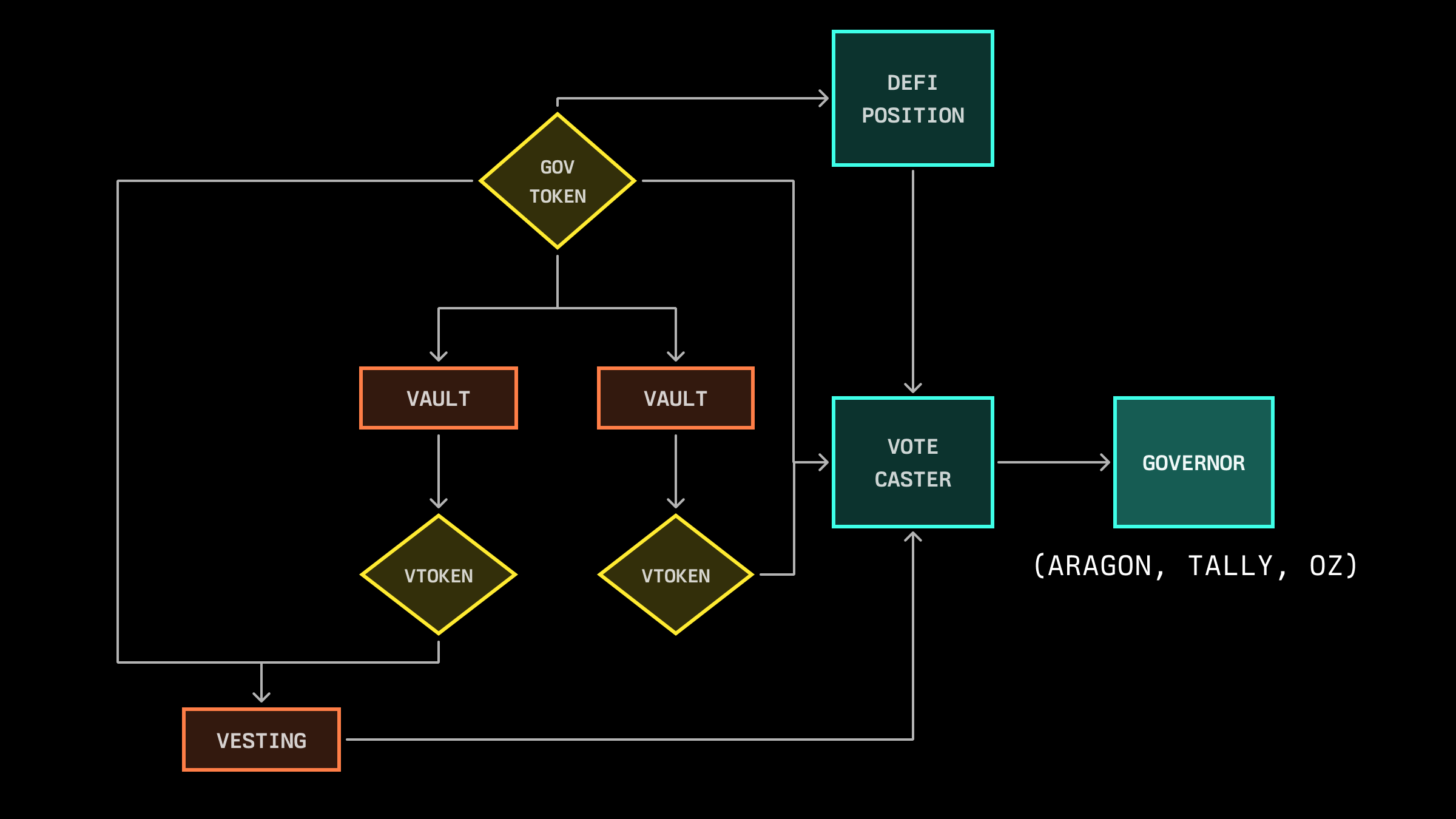
The vault system implements this unification by converting staked governance tokens into vTokens—non-rebasing ERC20 tokens representing proportional vault shares. vToken quantities remain constant during vault activities (deposits, withdrawals, slashing), providing stable stake representation. These tokens map to underlying governance tokens through Vault view functions, creating an on-chain price oracle with historical tracking capabilities. This design enables vTokens to participate in vesting mechanisms alongside native governance tokens, maintaining full utility while staked.
Governance tokens can extend beyond direct staking into DeFi applications, where their LP positions can serve as stake collateral. These positions maintain vesting compatibility, though they require additional implementation complexity compared to standard token vesting mechanisms.
In this implementation, the VoteCaster contract interfaces directly with governor contracts (such as Aragon, Tally, or OpenZeppelin), consolidating governance-equivalent balances for voting rights calculation. It is worth noting that this approach requires the ability to access historical amounts of all these tokens. Symbiotic vaults' built-in state-tracking mechanisms natively support this.
What is Collateral Abstraction?
These aforementioned implementations scratch the surface of an emerging research field and can be used in combination. Symbiotic's modular design enables flexibility through abstraction, opening doors to numerous additional possibilities: improving veToken utility, enhancing security through complex DeFi strategies, and more. Ultimately, Collateral abstraction can be defined through three core components:
- Collateral: Non-rebasing ERC20 tokens that either maintain direct value correlation with external assets or implement independent valuation mechanisms
- Vault: Management layer handling stake administration, position tracking, and value verification
- Burner: Configurable execution contracts implementing slashing logic across different stake types
This architecture transforms capital efficiency in blockchain networks. By expanding stake composition beyond simple token locking to include derivatives, DeFi positions, and cross-network assets, collateral abstraction eliminates the traditional trade-off between network security and capital utility. Symbiotic's implementation allows assets to remain in their native ecosystems while maintaining security guarantees through its vault and burner system.
The implementations explored—from DeFi positions to governance token systems—represent early ventures into this design space. The modular architecture enables customization while maintaining strong security assumptions. Network builders can create novel implementations, operators can optimize capital deployment, and researchers can explore new security models.
We invite the community to build on these foundations. The design space for collateral abstraction remains largely unexplored, with opportunities spanning from new asset types to novel security mechanisms. If you are interested in learning more or collaborating with Symbiotic, reach out to us here.









