Today, we are excited to announce the initial deployment of the Symbiotic protocol. This launch marks the first milestone towards the vision of a permissionless shared security protocol that enables effective decentralization and alignment for any network.
The Symbiotic protocol is a neutral coordination framework that introduces novel primitives for modular scaling.
This focus brings unique benefits to Symbiotic participants:
- Flexibility through Modularity
Networks control all aspects of their (re)staking implementation, including collateral assets supported, asset ratios and caps, node operator selection mechanics, rewards, slashing, and associated resolving mechanisms. All participants can flexibly opt in and out of shared security arrangements coordinated through Symbiotic. - Risk Minimization through Immutability
Non-upgradeable core contracts on Ethereum remove external governance risks and single points of failure. Our minimal, yet flexible contract design minimizes execution layer risks. - Capital Efficiency through Restaked Collateral
A permissionless, multi-asset, and network-agnostic design enables scalable and capital-efficient sourcing of economic security. An evolving operator-centric cross-network reputation system will further enhance capital efficiency for network builders.
The Evolution of Shared Security
Decentralized networks require coordination mechanisms to incentivize and ensure infrastructure operators conform to the rules of the protocol. In 2009, Bitcoin introduced the first trustless coordination mechanism, bootstrapping a decentralized network of miners providing the service of digital money via Proof-of-Work. The evolution towards Proof-of-Stake refined the model by focusing on economic collateral instead of raw computing power. Shared security implementations utilize the security of existing ecosystems, unlocking a safe and streamlined path to decentralize any network.
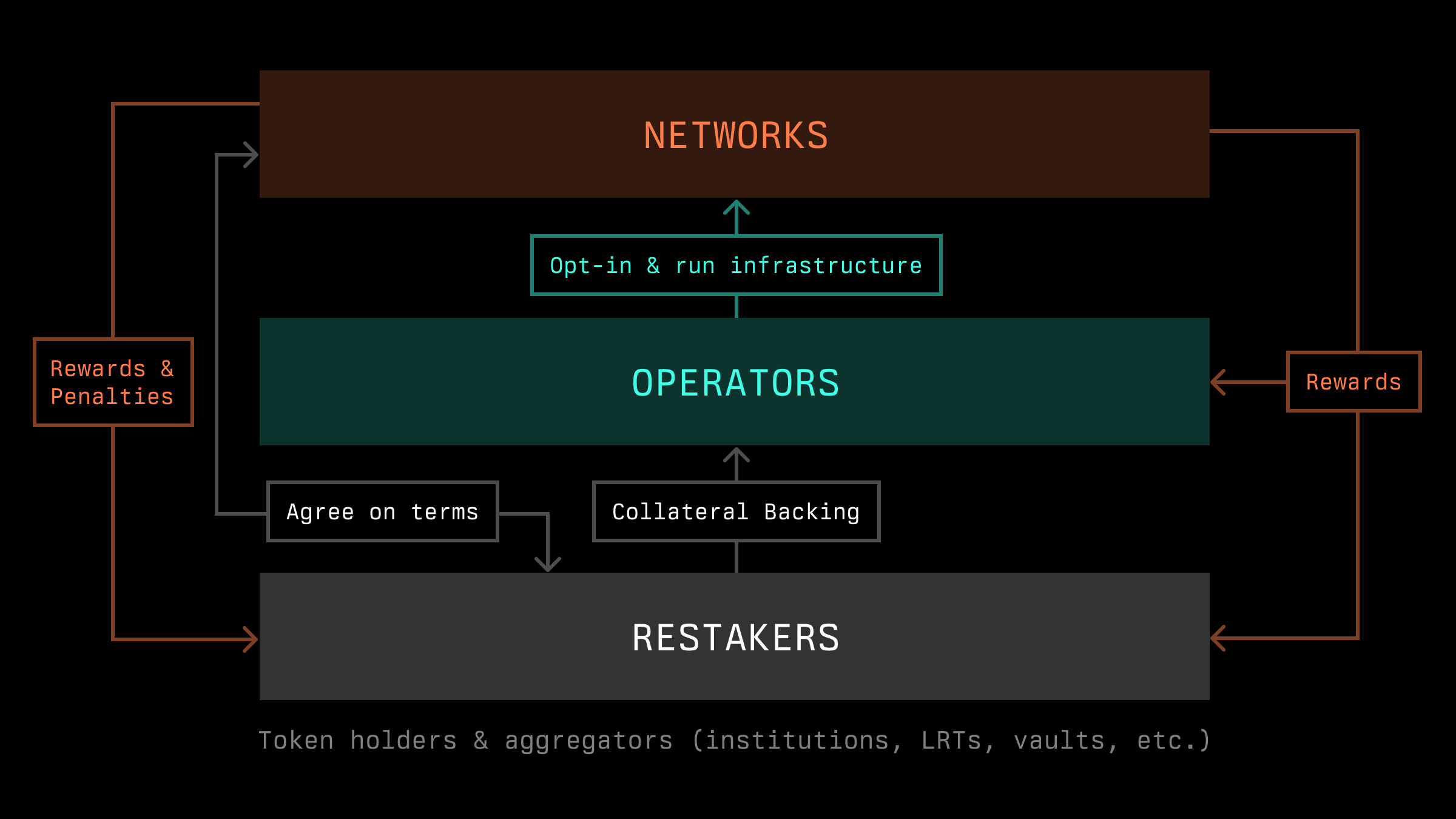
Symbiotic is a shared security protocol that serves as a thin coordination layer, empowering network builders to control and adapt their own (re)staking implementation in a permissionless manner.
Announcing the Symbiotic Ecosystem
Of the various actors required to bootstrap a restaking ecosystem, decentralized networks that require economic security play an outsized role in its growth and health.
Symbiotic is highly flexible and opens up an entirely new design space. Protocols at any stage of their decentralization journey can leverage Symbiotic. Projects can launch a trust-minimized and decentralized network with established operators on day one, expand the operator set of their existing ecosystem, increase the cost of attack by introducing additional stake, or align ecosystems by incorporating any configuration of multiple tokens in their network’s collateral base.
We are thrilled to highlight our initial network partners that are exploring Symbiotic’s restaking primitives:

- Ethena is integrating Symbiotic with LayerZero's Decentralized Verifier Network (DVN) framework to bring Ethena assets such as $USDe cross-chain secured by staked $ENA. This is the first of several pieces within their infrastructure and system that will look to leverage staked $ENA.
- Built by Chainbound, Bolt is a protocol that enables Ethereum block proposers to make credible commitments, such as trustless pre-confirmations, and plans to leverage Symbiotic for operator set restaking and slashing.
- Hyperlane is exploring a Symbiotic-powered Interchain Security Module (ISM) for their modular interoperability framework.
- Kalypso by Marlin is a circuit-agnostic ZK Proof Marketplace supporting private inputs, using Symbiotic restaking to provide liveness and response times guarantees for proof generation.
- Fairblock is working with Symbiotic to explore dynamic cryptography service networks (CSNs) that are secured through (re)staked assets and tailored to applications requiring different security parameters, performance, and usability trade-offs.
- Aori is looking to integrate Symbiotic restaking with stablecoin assets to hold market makers and solvers accountable when interacting with their high-frequency orderbook protocol.
- Drosera is working with the Symbiotic team on researching and implementing restaking-secured application security for Ethereum Layer-2 solutions.
- Ojo is a cross-chain oracle network that is going to increase their economic security through a Symbiotic restaking implementation.
- By integrating Symbiotic customizable security with their customizable compute infrastructure, Blockless empowers builders to create secure, network-neutral applications with full autonomy and flexibility over shared security.
- Rollkit is exploring to integrate Symbiotic restaking into their modular stack that facilitates launching sovereign rollups on Celestia; Symbiotic will initially help provide accountability to rollup sequencers, with the long-term goal of the integration being sequencer decentralization.
- Cycle Network is a blockchain-agnostic, unified liquidity network that will use Symbiotic to power its shared sequencer.
- Stork is looking to integrate Symbiotic restaking, enhancing trustlessness in on-chain data utilization.
- Aizel is building a verifiable AI network, researching to leverage Symbiotic restaking for different node roles to ensure verifiability from inference to execution.
- Mind Network will leverage Symbiotic's universal restaking services combined with FHE to enhance economic and consensus security in decentralized networks.
- DOPP is building a fully onchain options protocol that is researching Symbiotic restaking to help decentralize its oracle network for option-specific price feeds.
We aim to make Symbiotic the most developer-friendly home for building sovereign, trust-minimized applications and infrastructure.
Our Fundraise from Paradigm and cyber•Fund
To further our mission, we’ve raised a $5.8m seed round from Paradigm and cyber•Fund, two deeply crypto-native investors that share our long-term vision for an open, permissionless restaking economy.
We are excited to see and support what will be built on top of Symbiotic’s shared security primitive. If you are interested in collaborating with Symbiotic, reach out to us here.
Regarding Collateral Tokens and Deposit Limitations
The Symbiotic protocol is neutral and permissionless.
The goal of early deposits is to sustainably scale Symbiotic’s shared security platform. Collateral assets (re)stakeable through the main protocol interface (https://app.symbiotic.fi) will be capped in size during the initial stages of the rollout and will be limited to major token ecosystems, reflecting current market conditions in the interest of preserving neutrality. During further stages of the rollout, new collateral assets will be added based on ecosystem demand.